Cyber Security Awareness Month
Protecting Local Businesses, One Step at a Time
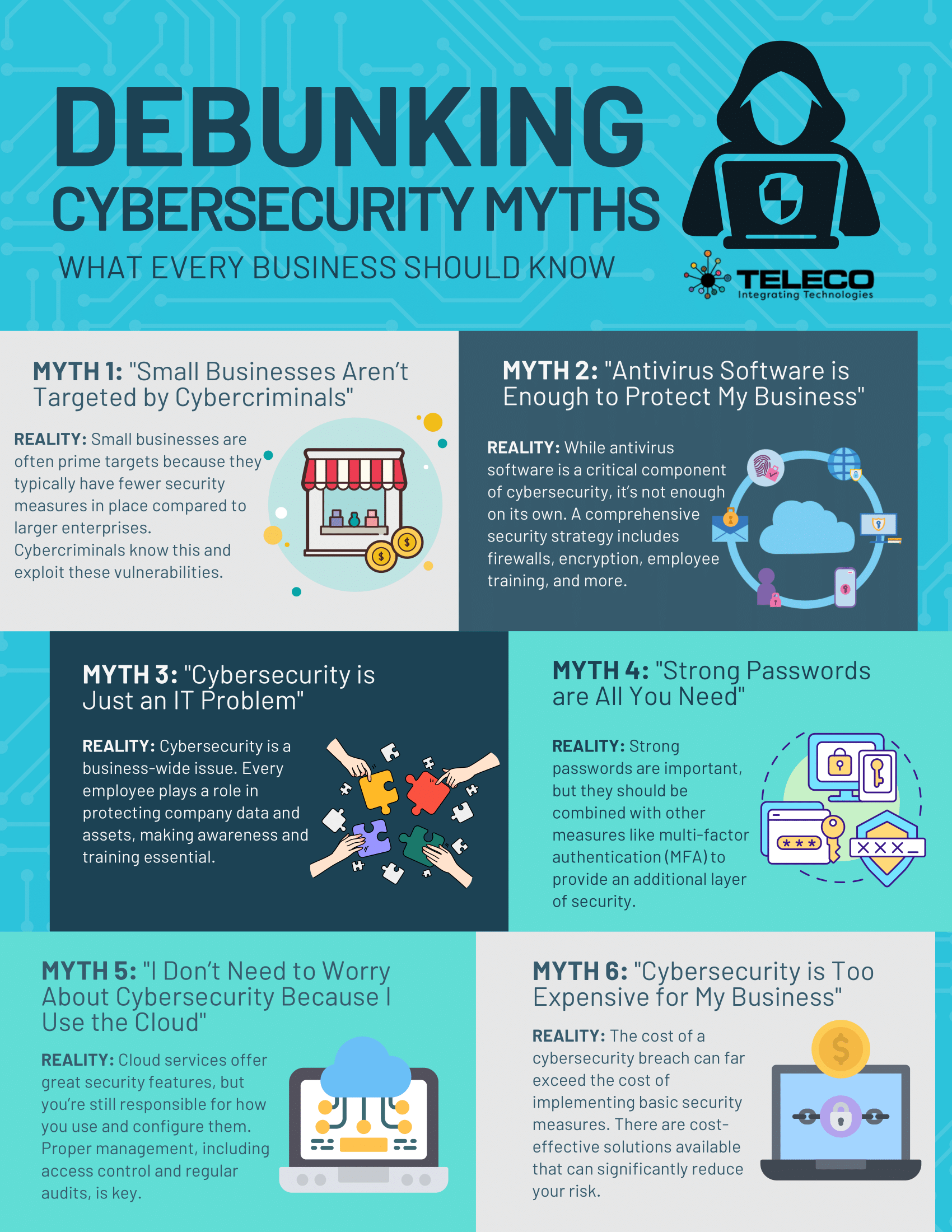
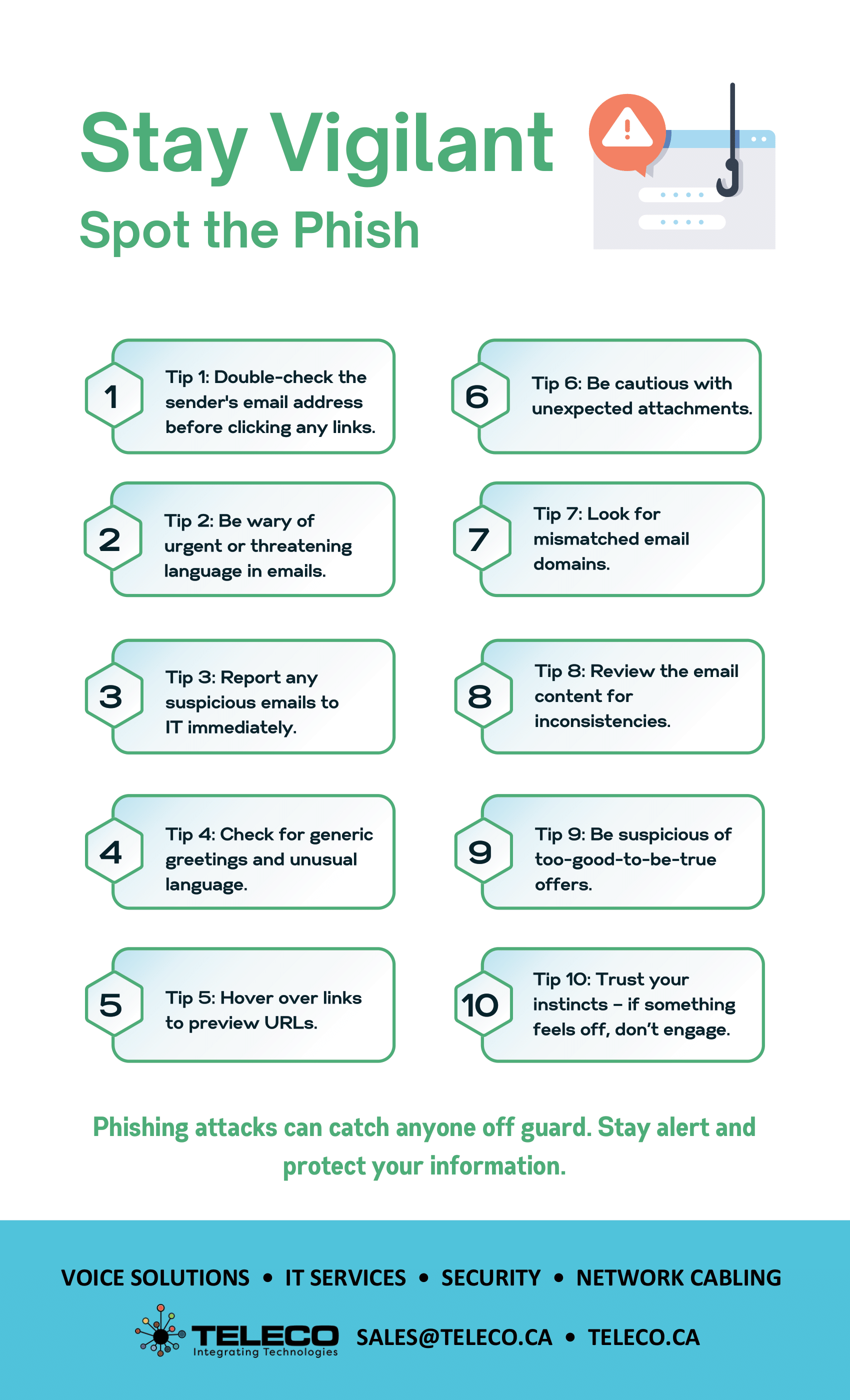
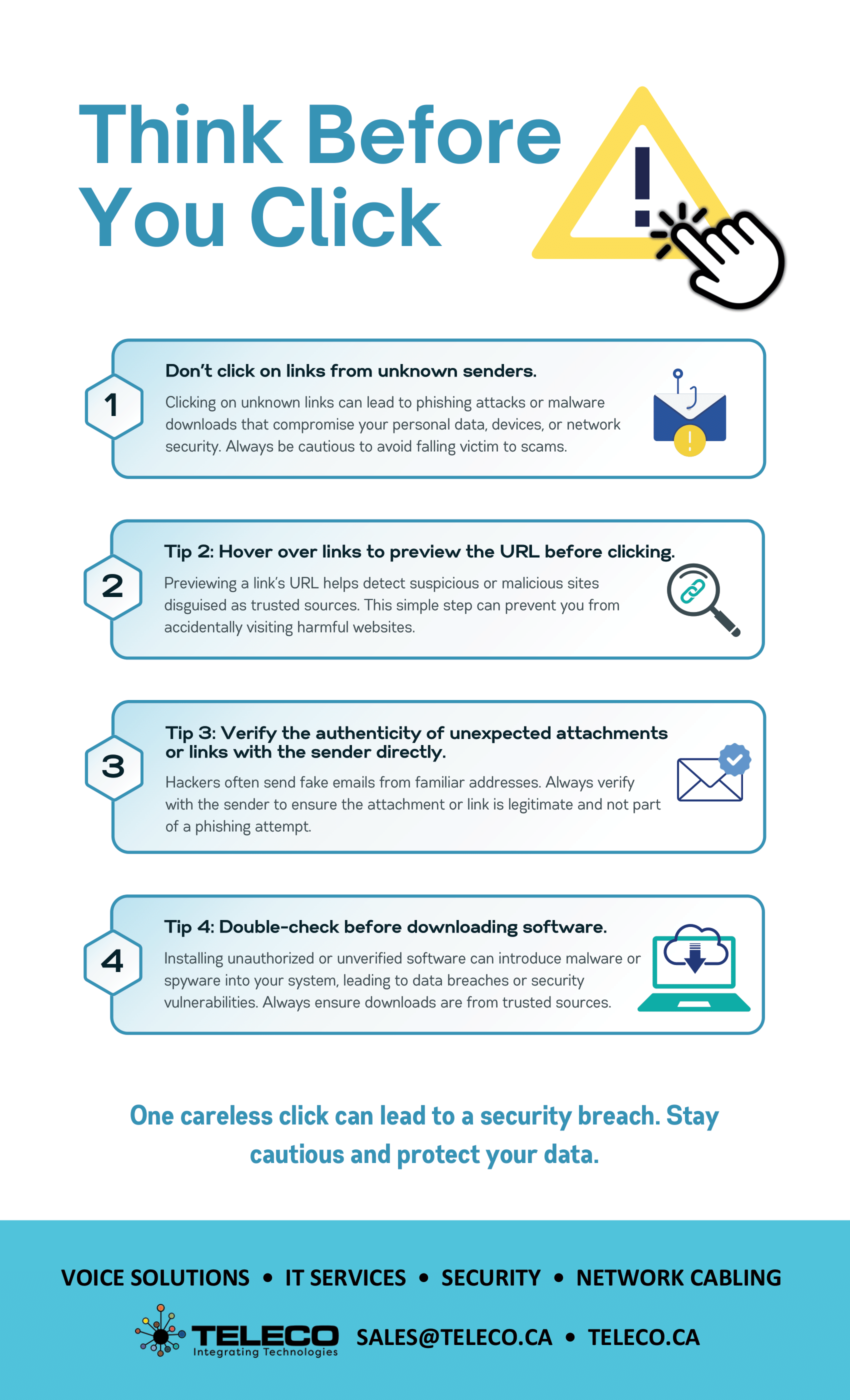
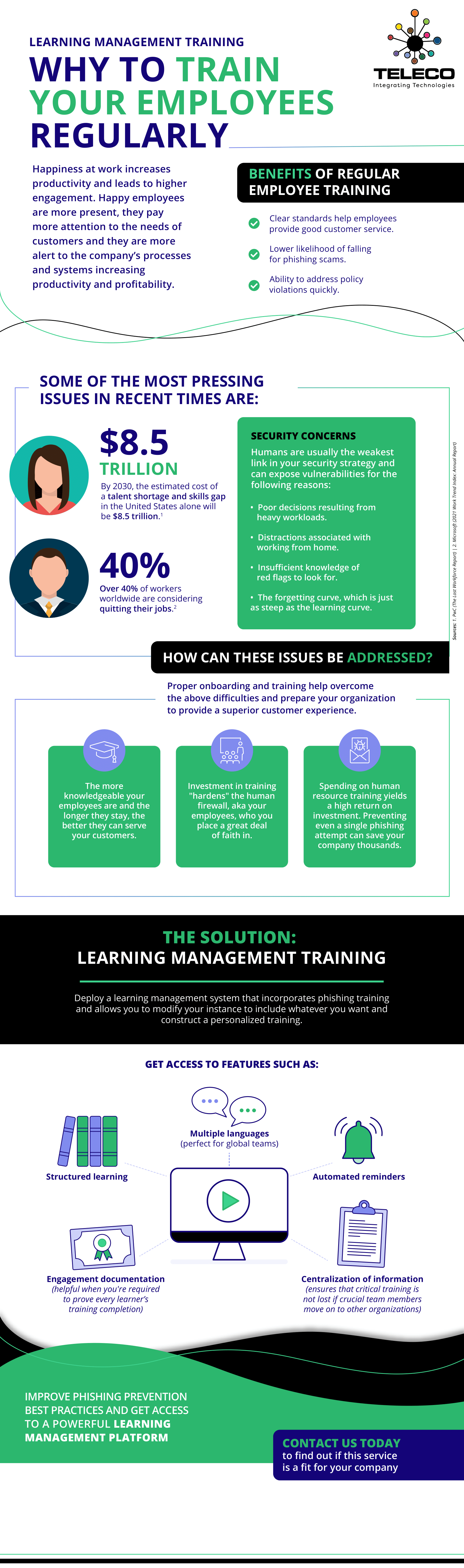
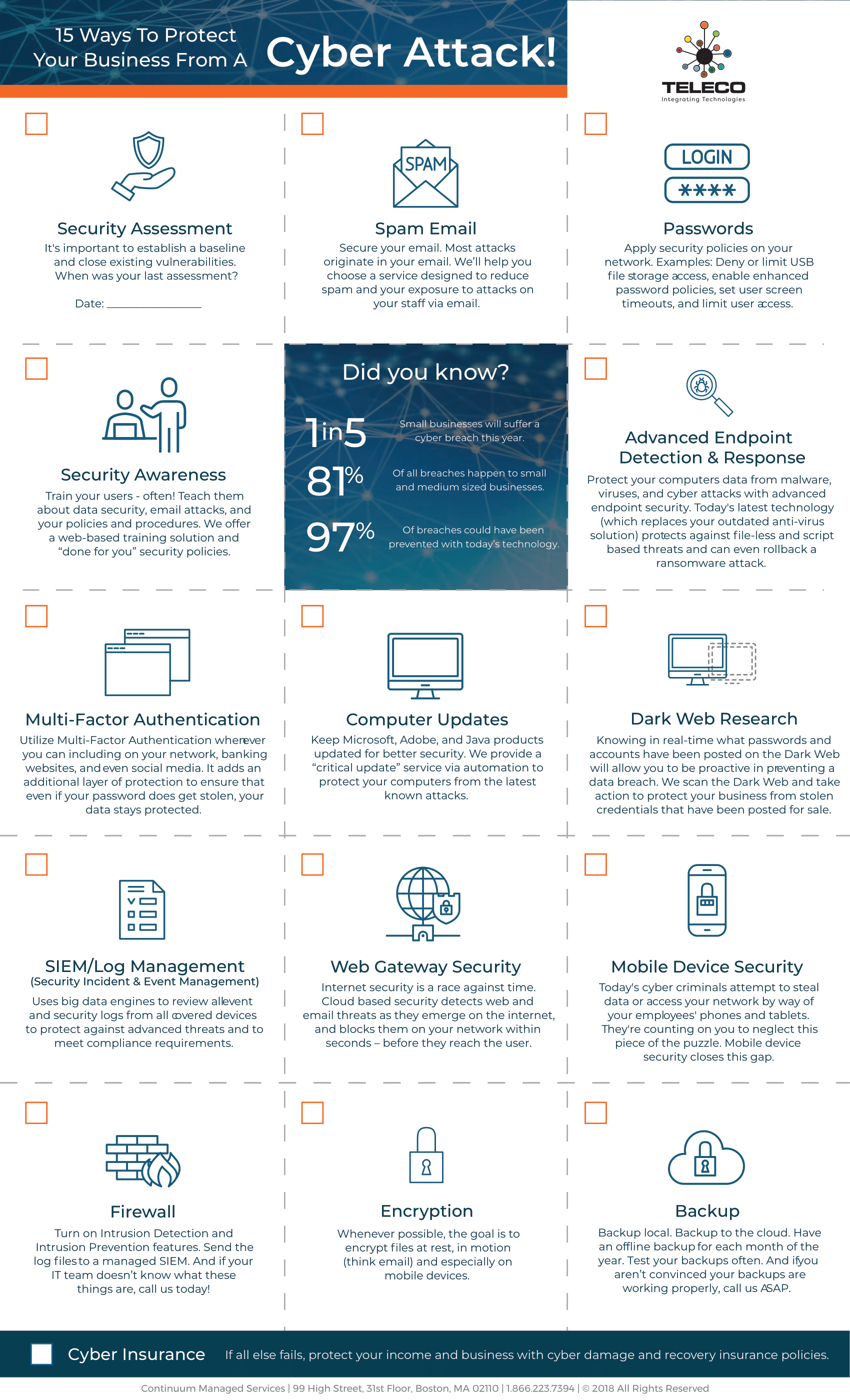
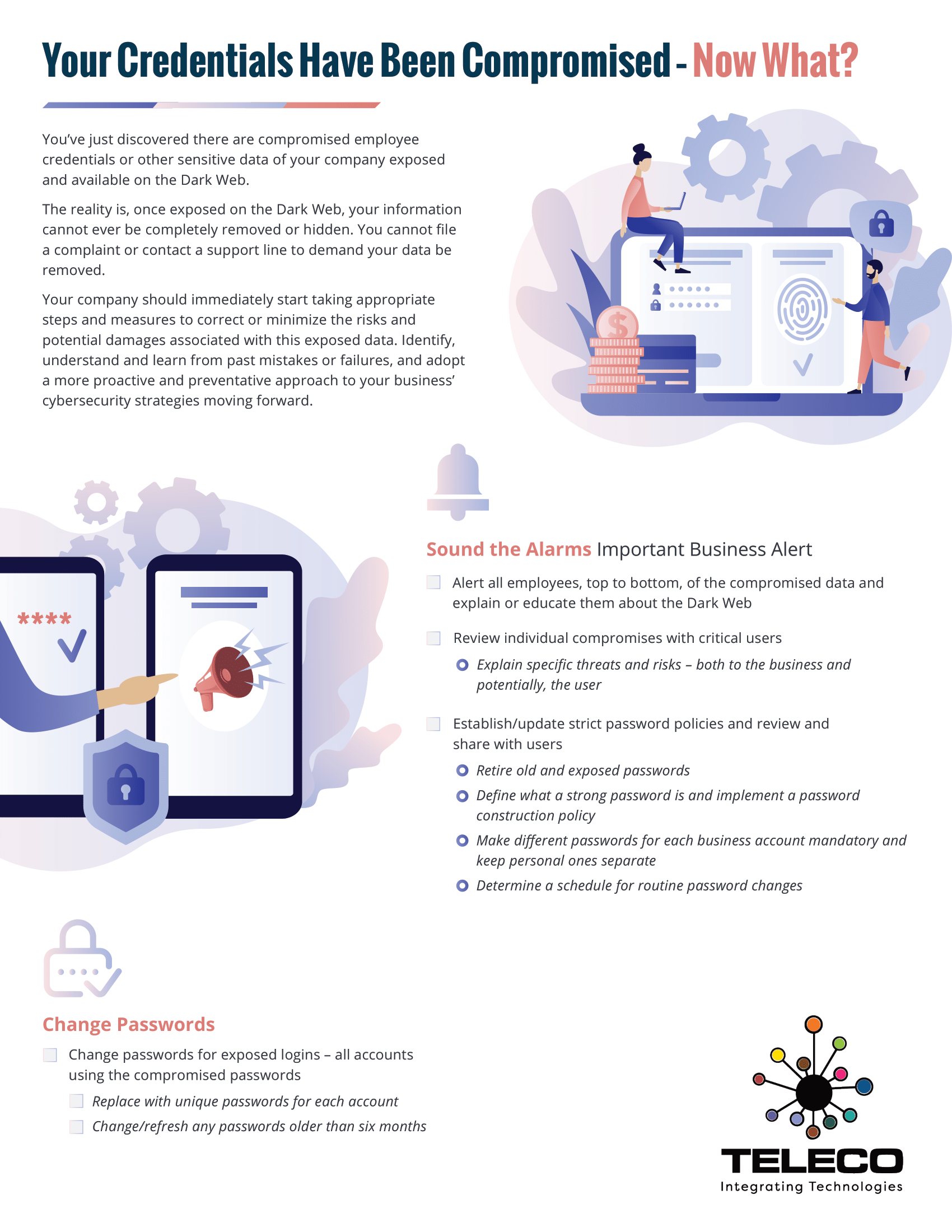
October is Cybersecurity Awareness Month, and at Teleco, we’re proud to support our community by making cybersecurity simple, approachable, and effective. For over 40 years, we’ve helped businesses integrate technology that not only works—but works securely.
That’s why this month, we’re giving away FREE Cybersecurity Kits to local businesses.
What’s Inside Your Cybersecurity Kit?
Each kit is designed to provide your team with practical tools and knowledge to strengthen your cybersecurity practices:
-
🔒 Webcam cover – A simple way to protect your privacy.
-
🖱️ Teleco mouse pad – Everyday reminders of cybersecurity best practices.
-
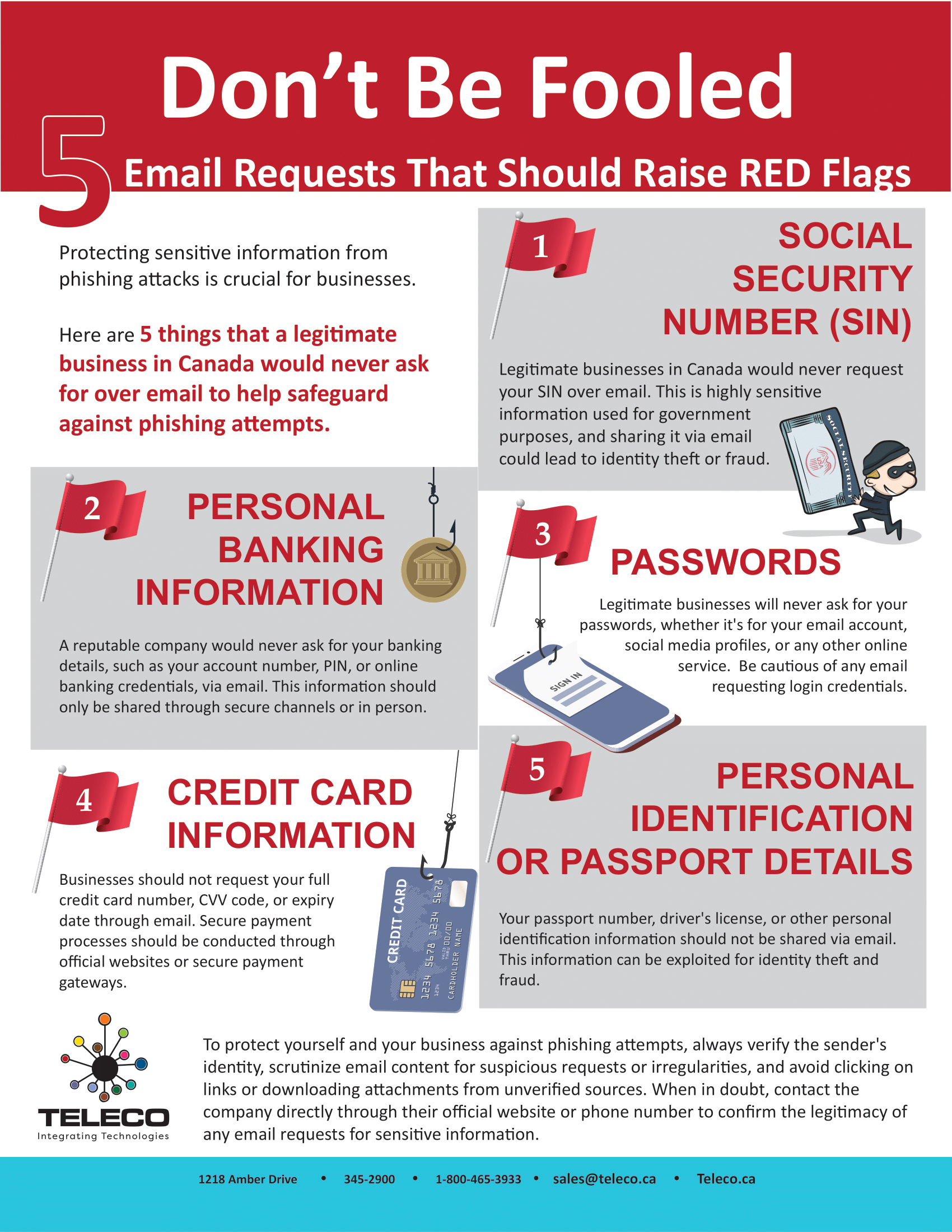
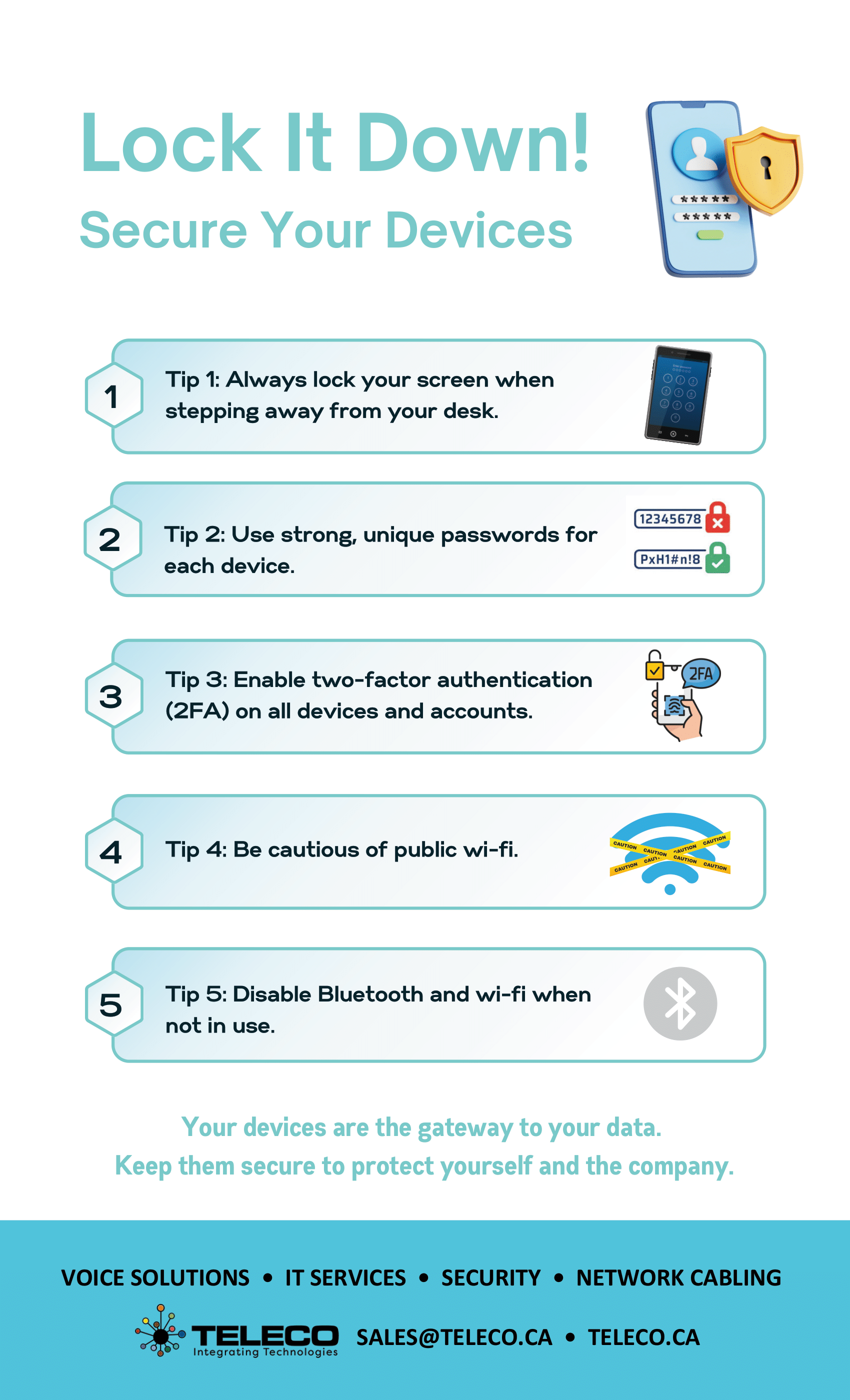
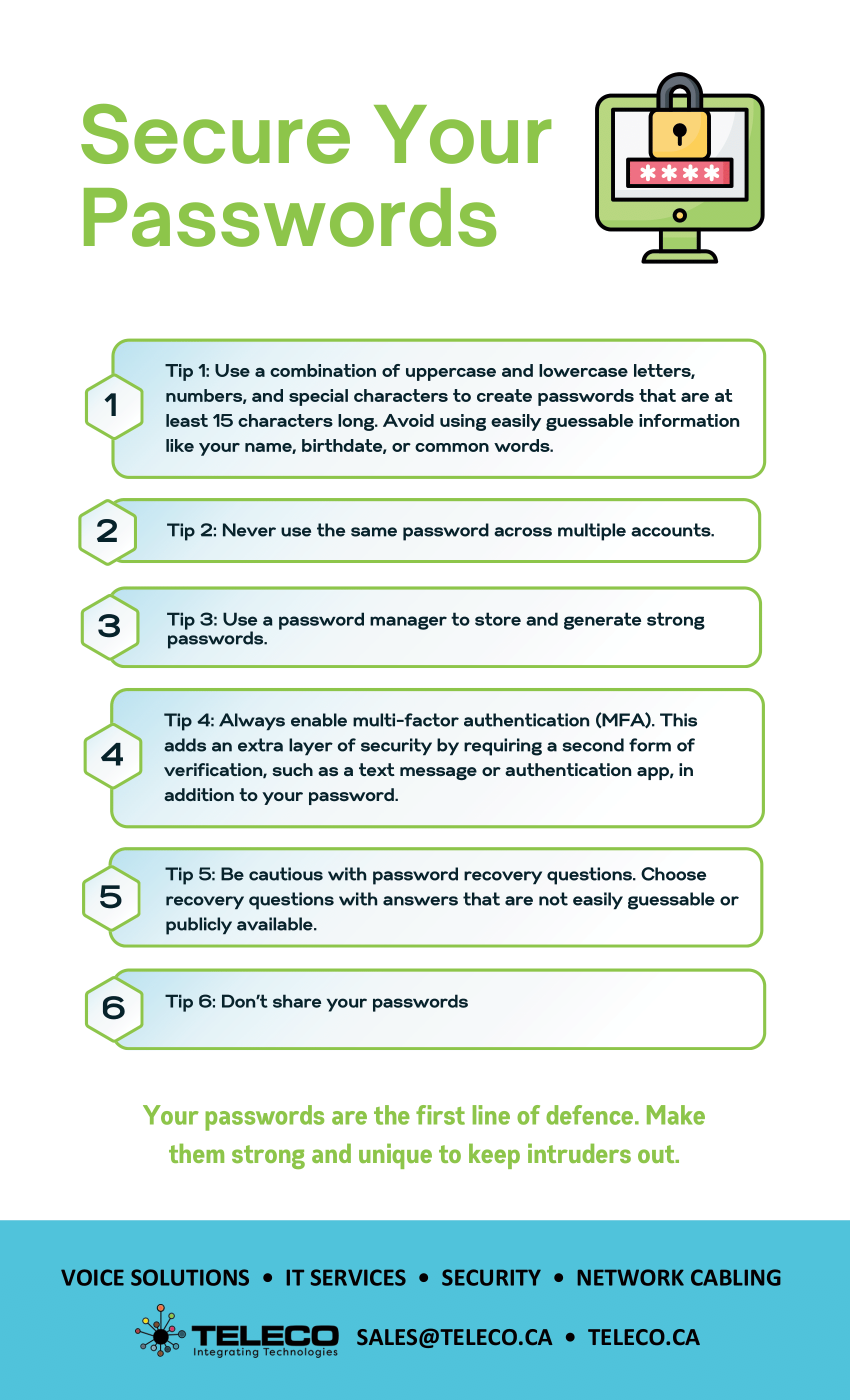
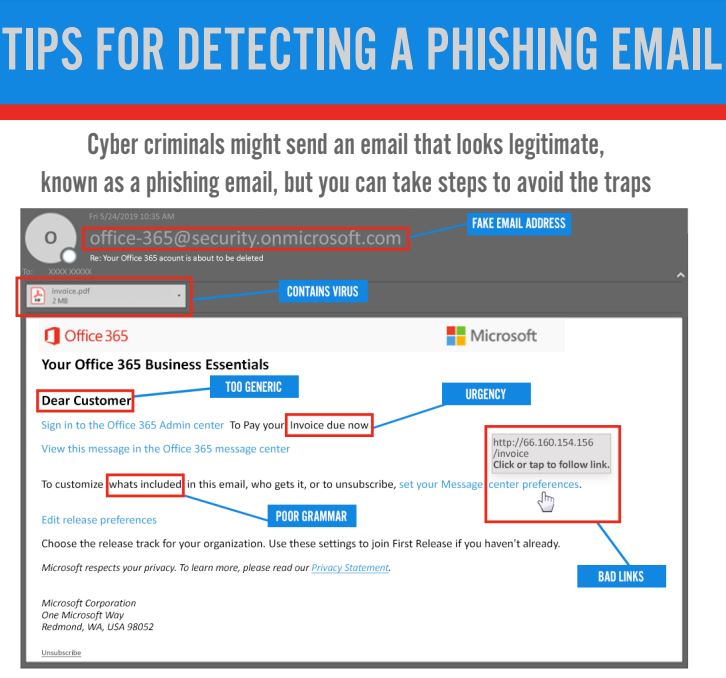
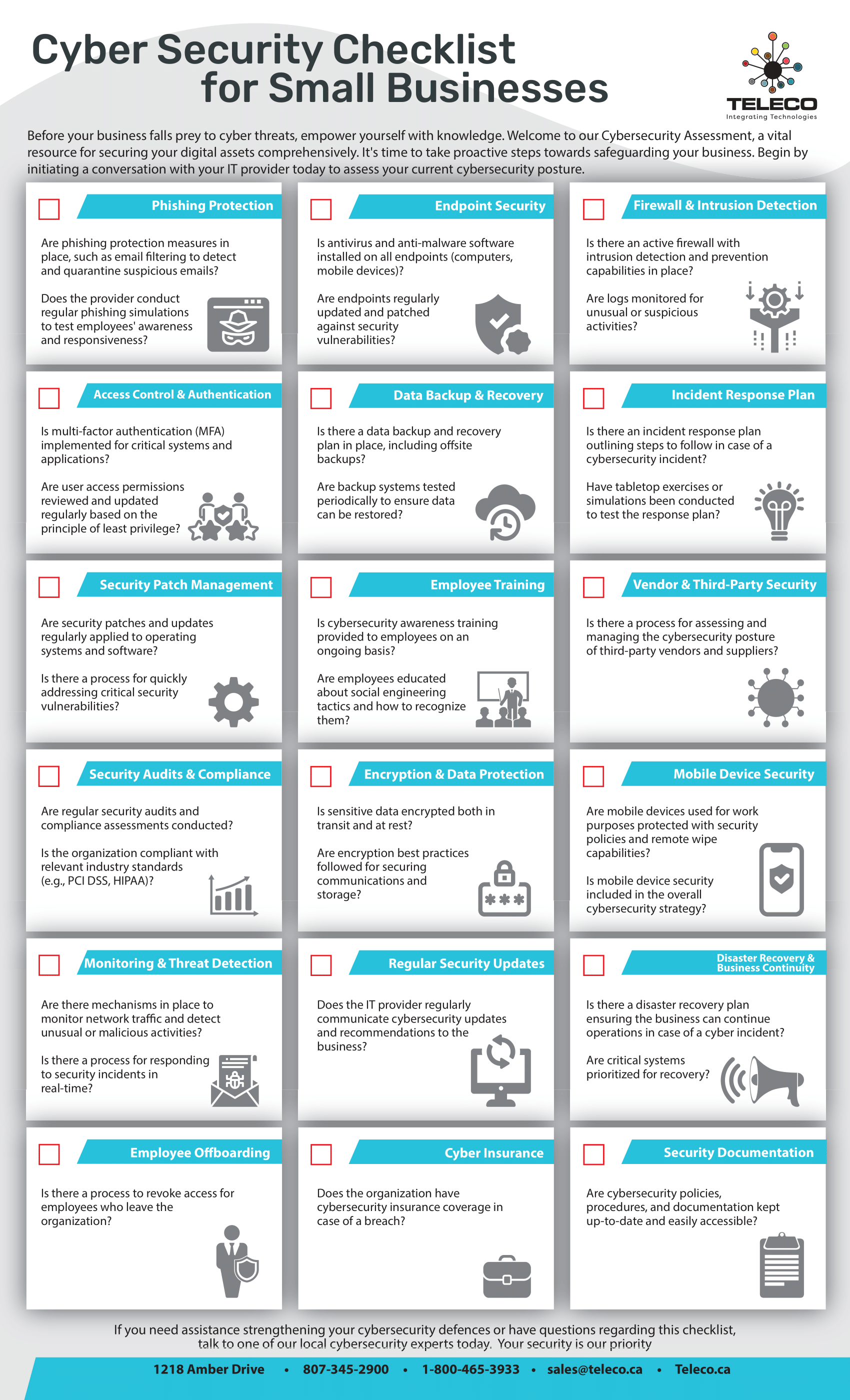
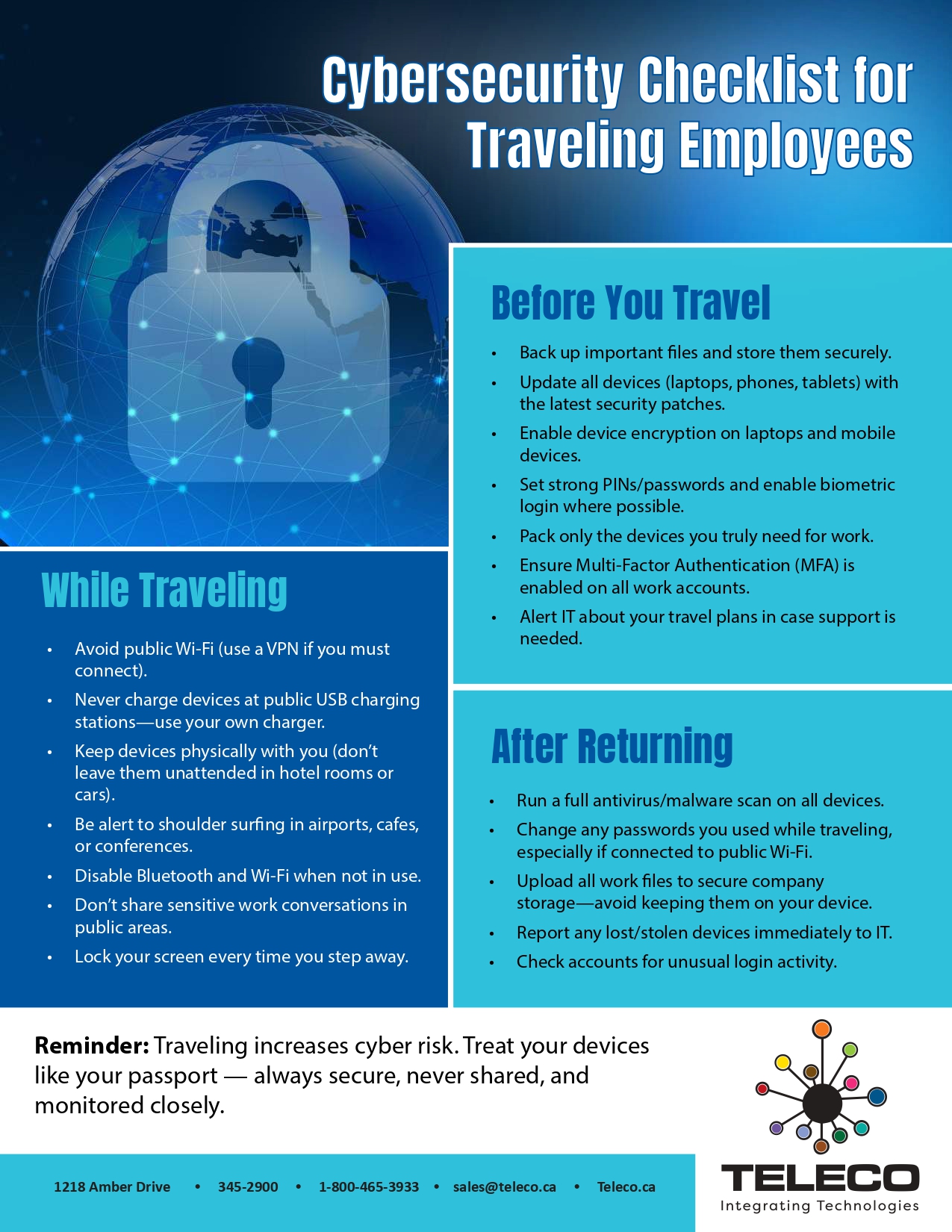
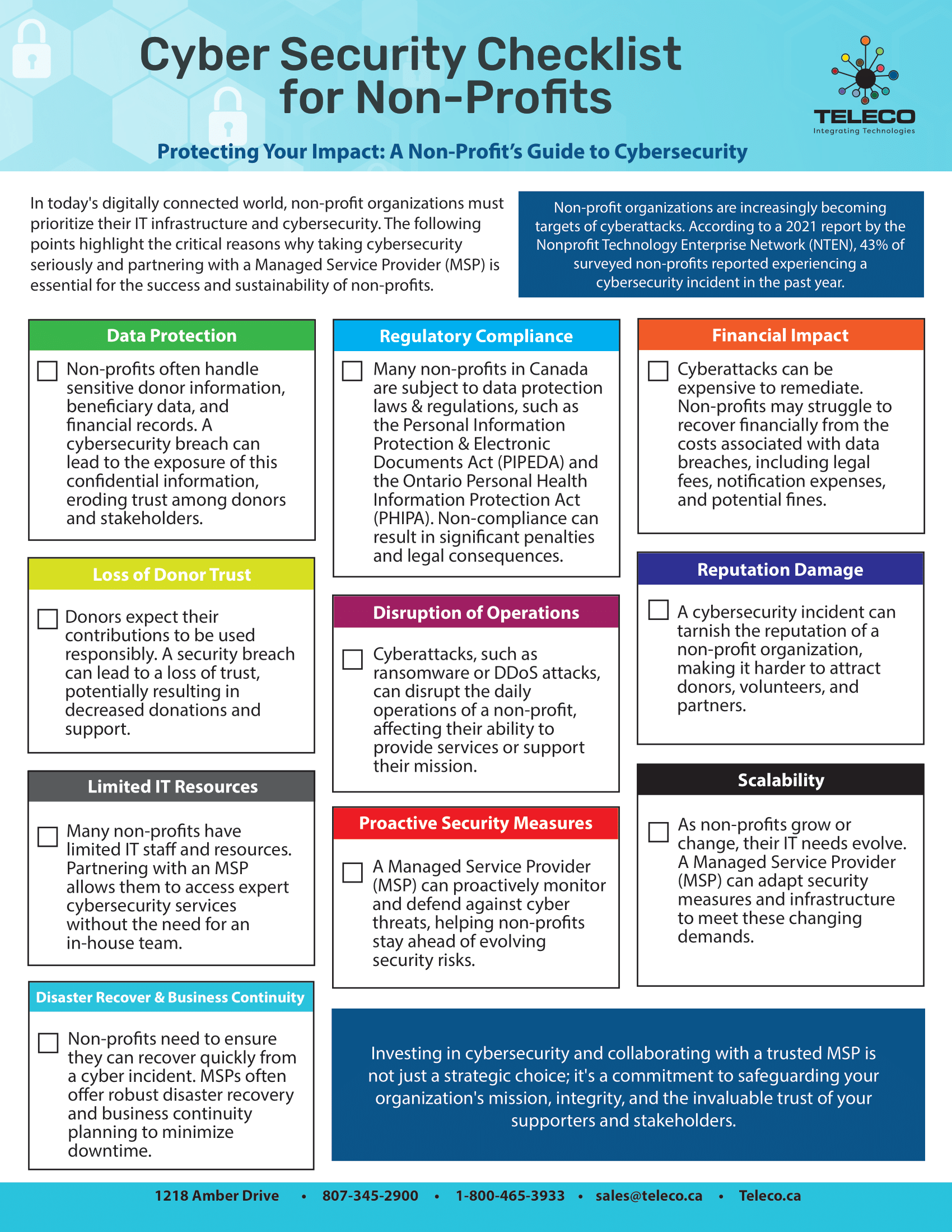
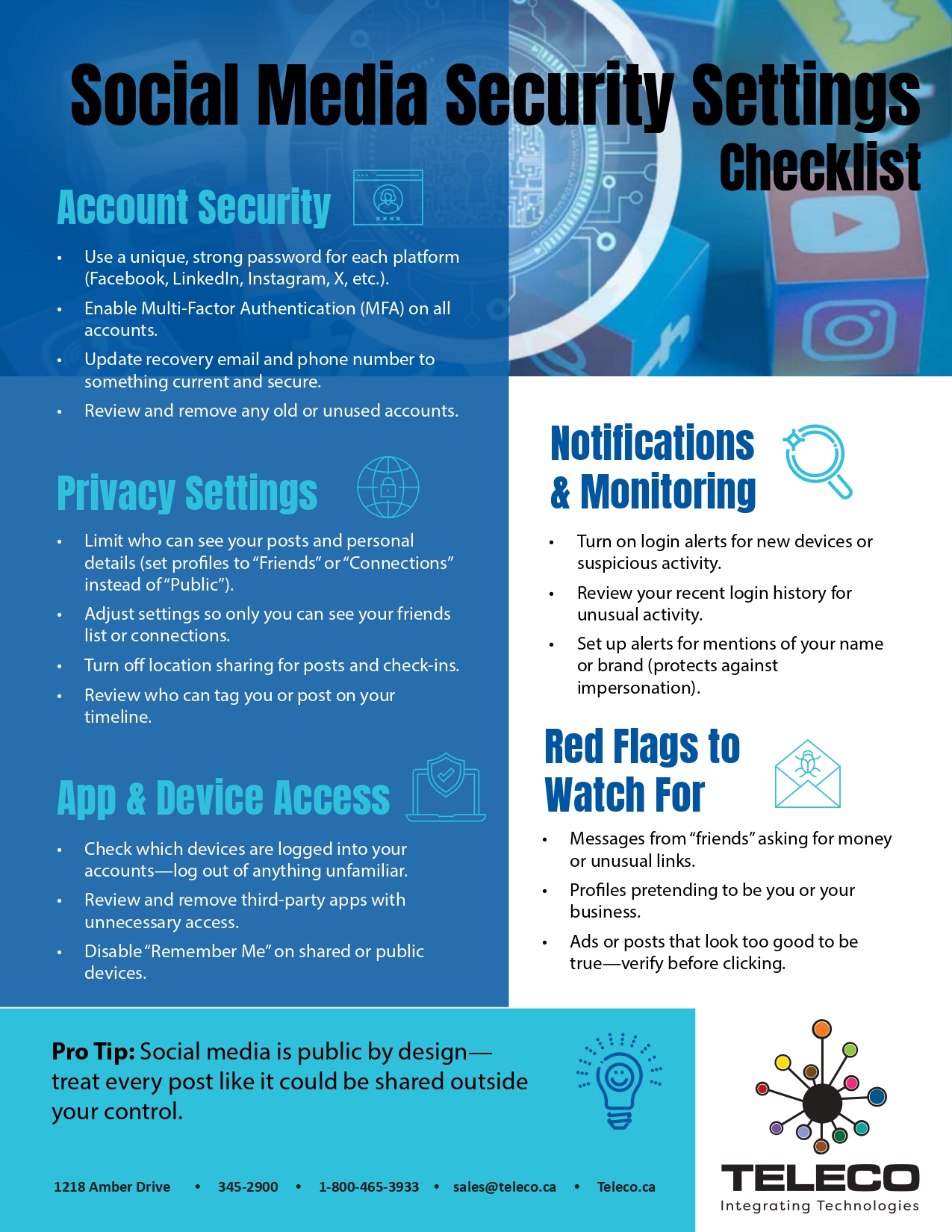
📋 Checklists & whitepapers – Step-by-step guides on how to defend your business from common cyber threats.
-
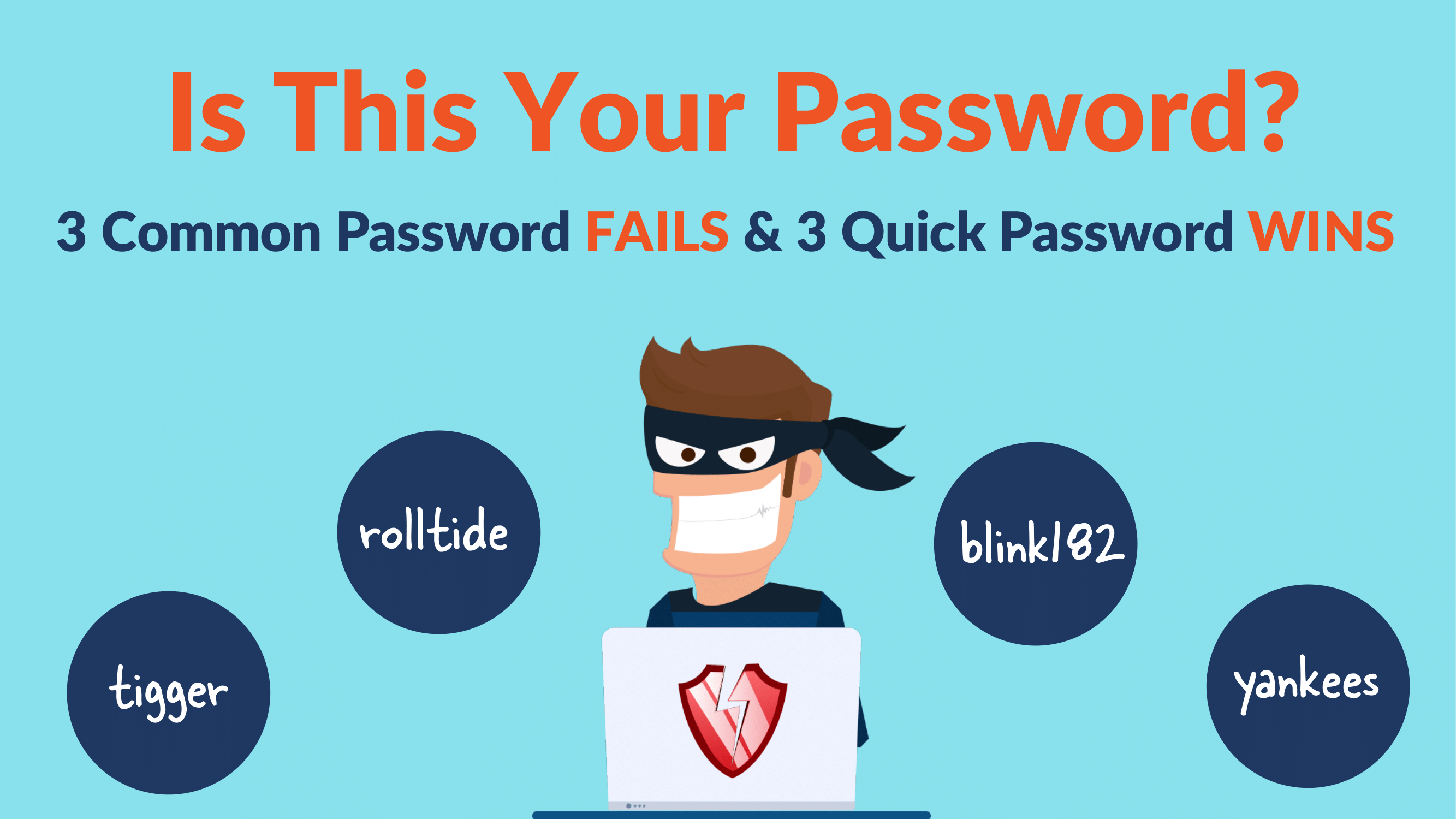
🛡️ Exclusive Offer: FREE Cyber Score Report – Includes a Dark Web Scan and Vulnerability Assessment to give you a clear view of your company’s cyber health.
Why We’re Doing This
Cyber threats don’t just target large enterprises—they affect organizations of every size, including local businesses right here in our community. At Teleco, we believe prevention starts with awareness, and with the right tools in hand, you can dramatically reduce your risks.
Claim Your Free Kit Today
Kits are available in limited quantities. Click below to request yours and take a proactive step toward protecting your business.